Startups’ primary focus is usually on growth and expansion, which can cause security to be overlooked or deprioritized. However, neglecting defensive measures can have serious consequences – data breaches, loss of intellectual property, and reputational damage. Limited resources, lack of expertise, and little time to focus on security matters are among the unique challenges that starting companies might face. As a result, they may not be adequately prepared to protect themselves and their customers from security threats. In this blog, we are going to highlight some of the obstacles that startups might encounter and share our experiences on how to tackle them effectively.
Improve network and application security
Protecting your network and application code is crucial for any business, and even more so for startups. Those companies need to prioritize safety from the outset and develop comprehensive protection strategies that include both network and application security. Here are some tips to enhance those aspects:
Network Segmentation
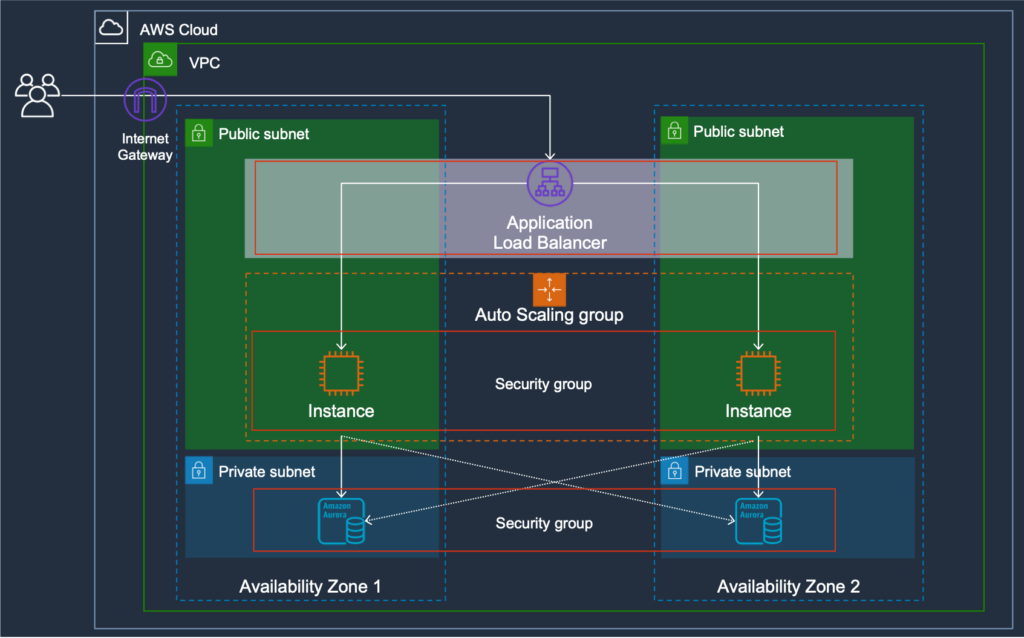
As a security expert, one of the most effective tools at your disposal is network isolation. We utilize Amazon Virtual Private Cloud (VPC) to isolate our resources from the public internet and establish a private network environment for all our customers. This allows us to fine-tune access control and monitor any abnormalities. Furthermore, in order to enhance network isolation, we employ a range of additional security measures including:
- Enterprise-grade firewalls
- Intrusion detection and prevention systems(IDPS)
- Virtual private networks(VPN).
These measures guarantee that all traffic exchanged between our servers and those of our customers is fully encrypted and secured.
Threat detection
For startups with limited resources, automating threat detection processes can be a game-changer. Automation can help to streamline the monitoring and detection of potential threats, reducing the workload on already stretched resources. Utilizing automated threat detection tools can also provide real-time alerts and insights, enabling startups to respond quickly to potential threats before they cause significant damage.
Amazon GuardDuty is an intelligent threat detection service that uses machine learning to identify potential security issues, such as compromised accounts or unauthorized access attempts. We use GuardDuty to monitor our AWS accounts for malicious activity and unauthorized access attempts.
Vulnerabilities detection
As a starting company, it is crucial to have a comprehensive vulnerability detection strategy in place. We utilize AWS Inspector, a critical component of our shielding infrastructure, to automatically assess our code for vulnerabilities and potential security issues. The service generates detailed reports with recommendations for remediation, allowing us to quickly address any potential security issues before they can be exploited by attackers. By proactively identifying vulnerabilities, we’re reducing the risk of data breaches and other security incidents. This is evidenced by our strong performance on all publicly available security testing platforms.
Data Encryption
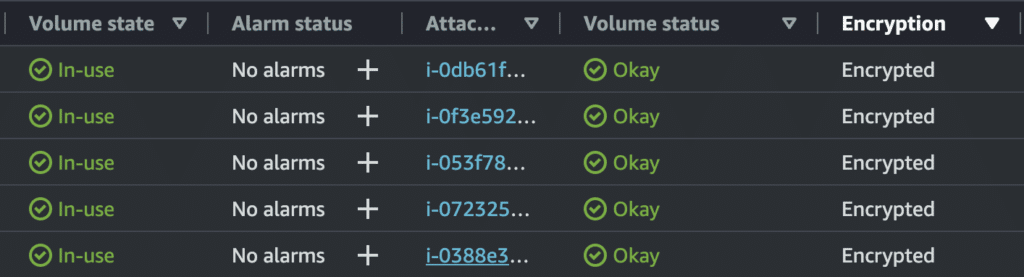
Encrypting your data is an inevitable task that you must undertake. However, implementing data encryption early in your startup can significantly improve your chances of avoiding a data breach. That’s why data encryption is an integral part of our overall security strategy at Kubit.
We guarantee end-to-end data security by utilizing encryption algorithms that meet industry standards. Our approach involves using Advanced Encryption Standard(AES) with a key length of 256 bits to encrypt all data at rest and in transit. AES 256-bit encryption is considered virtually unbreakable. This makes it one of the most robust encryption methods available, ensuring that our customers’ data is safeguarded with the highest level of security.
In addition to using strong cryptographic algorithms, we also operate a range of encryption-related technologies and protocols, including key management systems, digital certificates, and the latest secure hashing algorithms. For instance, we use key management systems(KMS) to securely generate, store, and manage encryption keys.
Monitoring
Effective security monitoring is crucial in today’s ever-evolving threat landscape, and it is especially important for startups that are vulnerable to cyber attacks due to their limited resources and visibility. Monitoring enables organizations to detect and respond to accidents promptly, reducing the impact of a potential security breach. By staying on top of those incidents and taking quick action, startups can prevent cybercriminals from exploiting vulnerabilities in their system and stealing sensitive data.
At Kubit, we recognize that continuous monitoring is critical for identifying potential threats in our infrastructure. To achieve this, we have implemented a sophisticated inspection system that enables us to detect and respond to incidents promptly.
We utilize anomaly detection as a critical component of our security monitoring strategy. This approach is able to identify deviations from typical activity in system data. By using machine learning algorithms to establish a baseline of normal behavior, we can automatically detect and alert our security team of any suspicious activity that may indicate a threat.
Conducting regular security assessments, including penetration testing, is crucial to ensure the integrity of our infrastructure and safeguard our customers’ data. While these assessments may require a significant investment of time and resources, they enable us to identify vulnerabilities and potential attack vectors that we may have overlooked.
Training
Employee training is an essential element of any startup’s security strategy. It’s essential to ensure that all employees are aware of the potential risks and threats to the company and are equipped with the knowledge and skills to prevent and respond to them. The training should cover a range of topics, including password management, phishing scams, social engineering tactics, and how to handle sensitive data.
One of the primary reasons why training is essential is that human error is one of the leading causes of security breaches. Employees may unwittingly click on a malicious link or inadvertently disclose sensitive information, exposing the company to significant risks. By providing regular security awareness training, startups can significantly reduce the likelihood of such incidents occurring.
To maintain a strong security culture at Kubit, we understand that team training is not a one-time event but an ongoing process. Regular updates and reminders are essential to keep security at the forefront of our minds. We ensure that all employees are trained in the latest security best practices.
Readiness and Reaction to Security Incidents
Having a plan in place for preparing and responding to incidents is an indispensable component of any startup’s security strategy. Regardless of how much effort is put into preventing security breaches, they can still happen. Hence, being well-prepared beforehand is crucial to ensure readiness and prompt action in the event of a security incident.
We understand that which is why we have a well-thought-out response plan in place. It outlines the necessary steps to take in the event of a security incident. Those include:
- Identifying the issue
- Containing the breach
- Restoring our platform to its normal state.
We also have a plan to keep all stakeholders informed promptly, including employees, customers, and partners, to maintain transparency and trust.
Furthermore, we don’t stop at having a plan, we regularly test it with drills and simulations to ensure its effectiveness and identify any areas for improvement.
Compliance
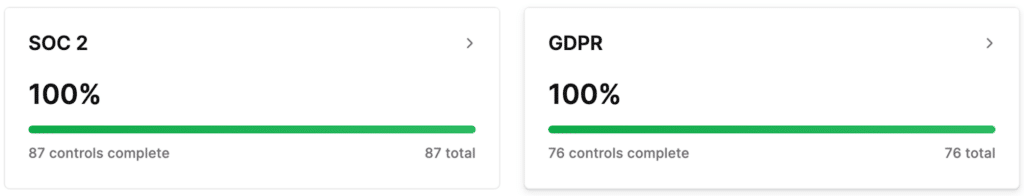
The handling of sensitive customer data by any company makes compliance with SOC 2 and GDPR crucial. SOC 2 is a set of standards that focuses on the security, availability, processing integrity, confidentiality, and privacy of customer data, while GDPR is a regulation that sets strict requirements for the collection, processing, and storage of personal data of EU citizens. Both SOC 2 and GDPR help to ensure customer data is handled with the utmost care and is protected from unauthorized access or disclosure.
Non-compliance with those standards can result in severe consequences, such as fines, legal action, and damage to the company’s reputation. In addition, failure to comply with these regulations can lead to data breaches, which can have a significant impact on the company’s operations and finances. It is crucial for companies to invest in the necessary resources to ensure compliance with these regulations, including implementing adequate security measures and providing employee training on data protection and privacy.
At Kubit, we take SOC 2 and GDPR compliance seriously, and we strive to maintain the highest standards for the protection of our customers’ data. We regularly assess our safety controls and processes to ensure we are in compliance with these regulations. Our security team works closely with other departments to implement policies and procedures, promoting data privacy and security, and we provide ongoing training and education to our employees to ensure that they understand their role in maintaining in-compliance status. By prioritizing adherence to both standards, we can provide our customers peace of mind that their data is being handled with the highest level of care and protection.
Final Thoughts
In conclusion, cybersecurity is a critical aspect of any startup’s operations. That’s why it should not be overlooked. By implementing strong security measures such as data encryption, network and application vulnerability scanning, company-wide training, and monitoring, startups can mitigate the risks of potential attacks and protect their customers’ data. Compliance with industry-recognized regulations such as SOC2 and GDPR demonstrates a commitment to the highest standards of security and data protection. This, in turn, can help build trust with customers and partners. While cybersecurity may require an initial investment of time and resources, the benefits of having a robust cybersecurity infrastructure far outweigh the costs.





